Amazon.fr - Practical Binary Analysis: Build Your Own Linux Tools for Binary Instrumentation, Analysis, and Disassembly - Andriesse, Dennis - Livres

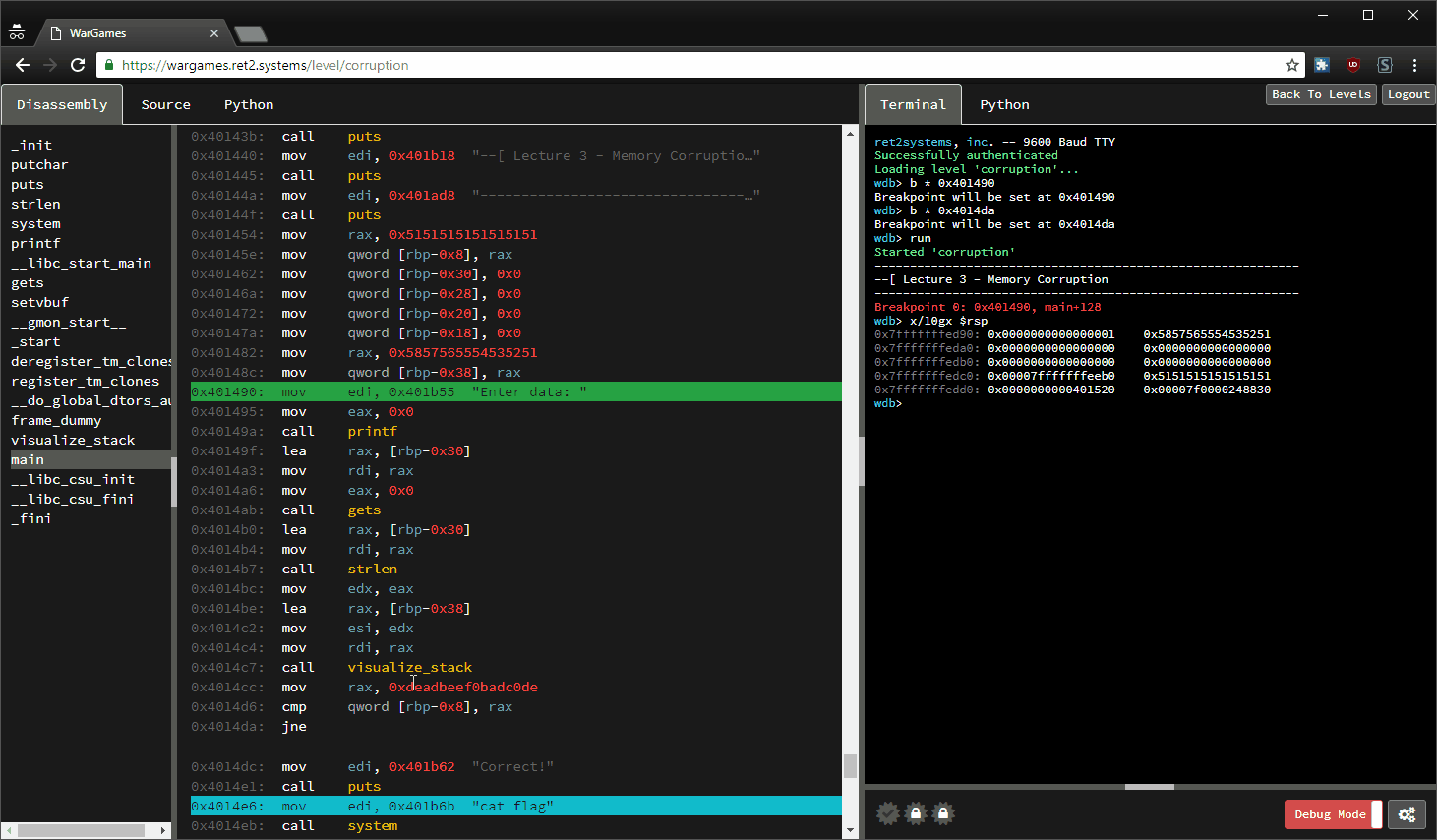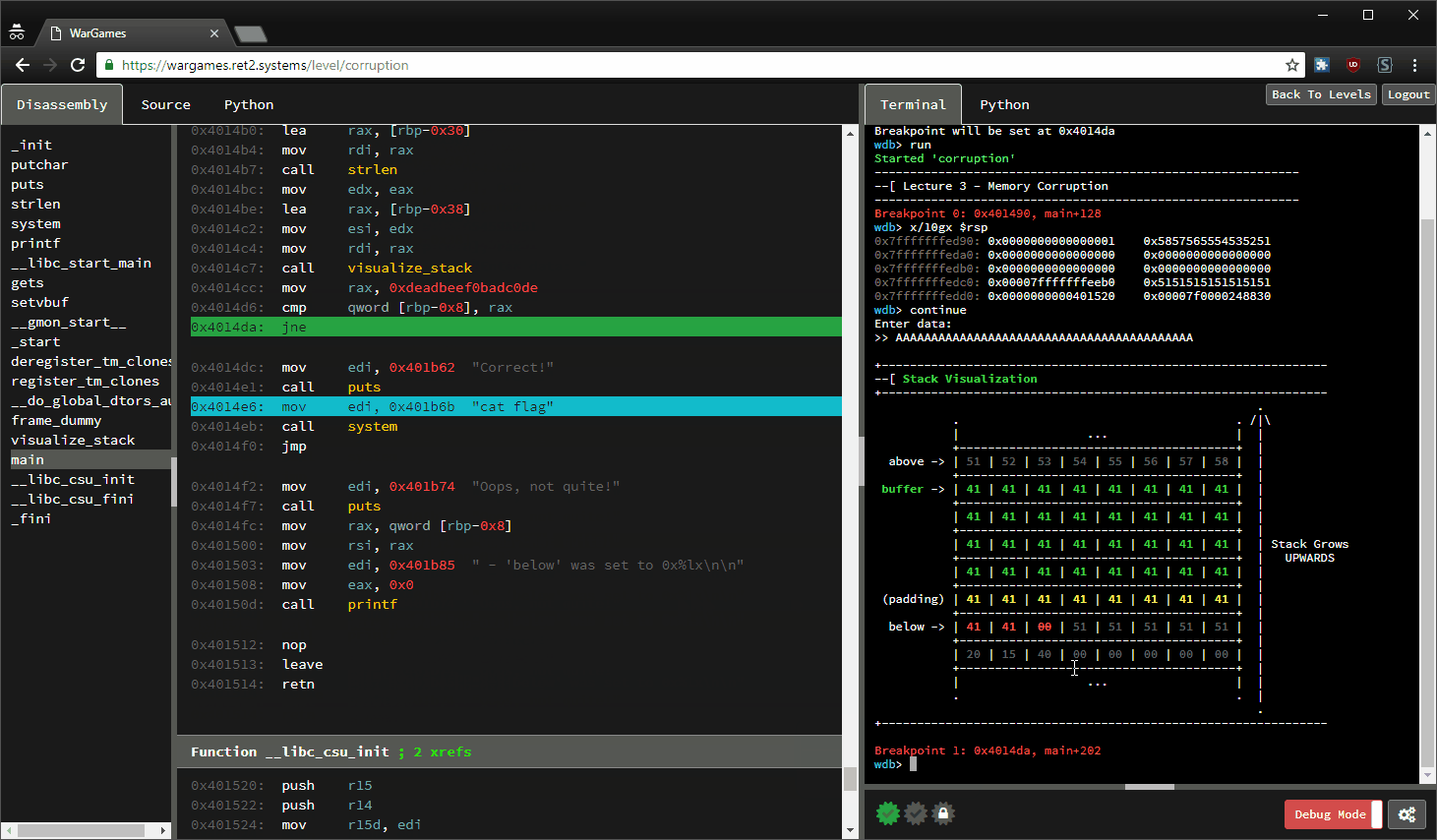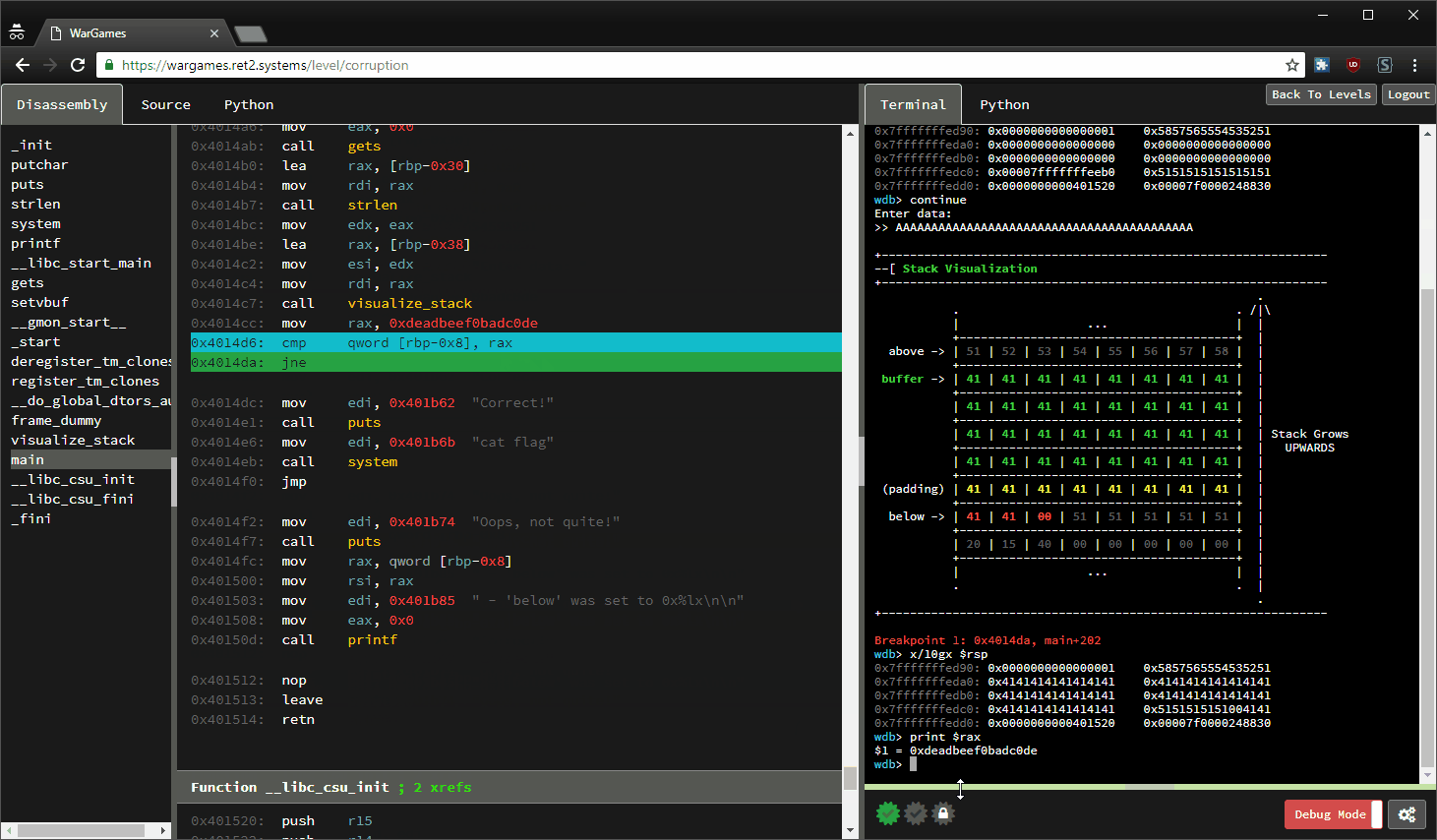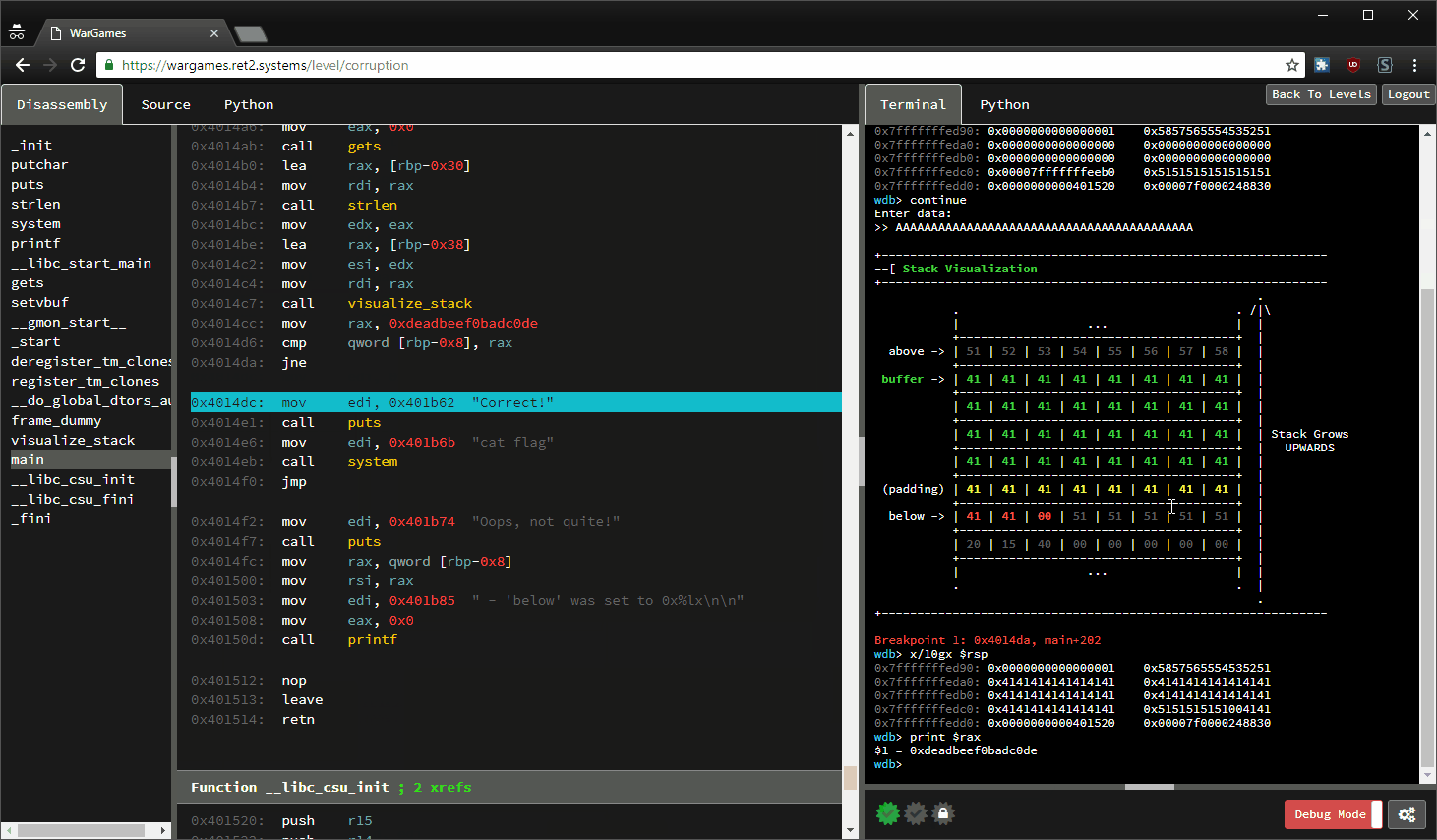
basic file exploit(100 points)— Binary Exploitation writeup | Pico CTF 2022 | by Karthikeyan Nagaraj | InfoSec Write-ups
GitHub - crake7/Binary-Exploitation-Tools: Automation of buffer overflows corrupting the Saved Return Pointer.







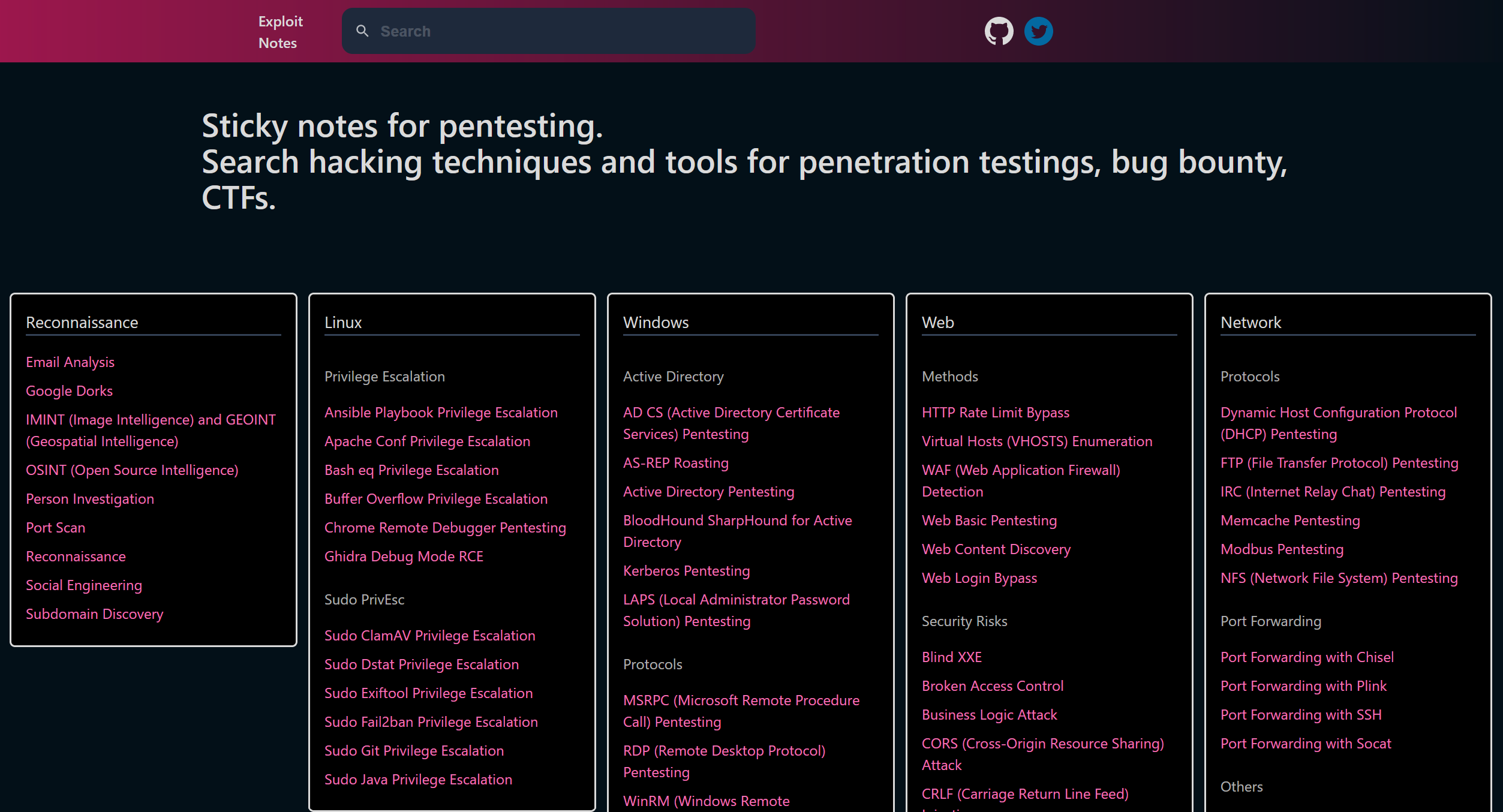
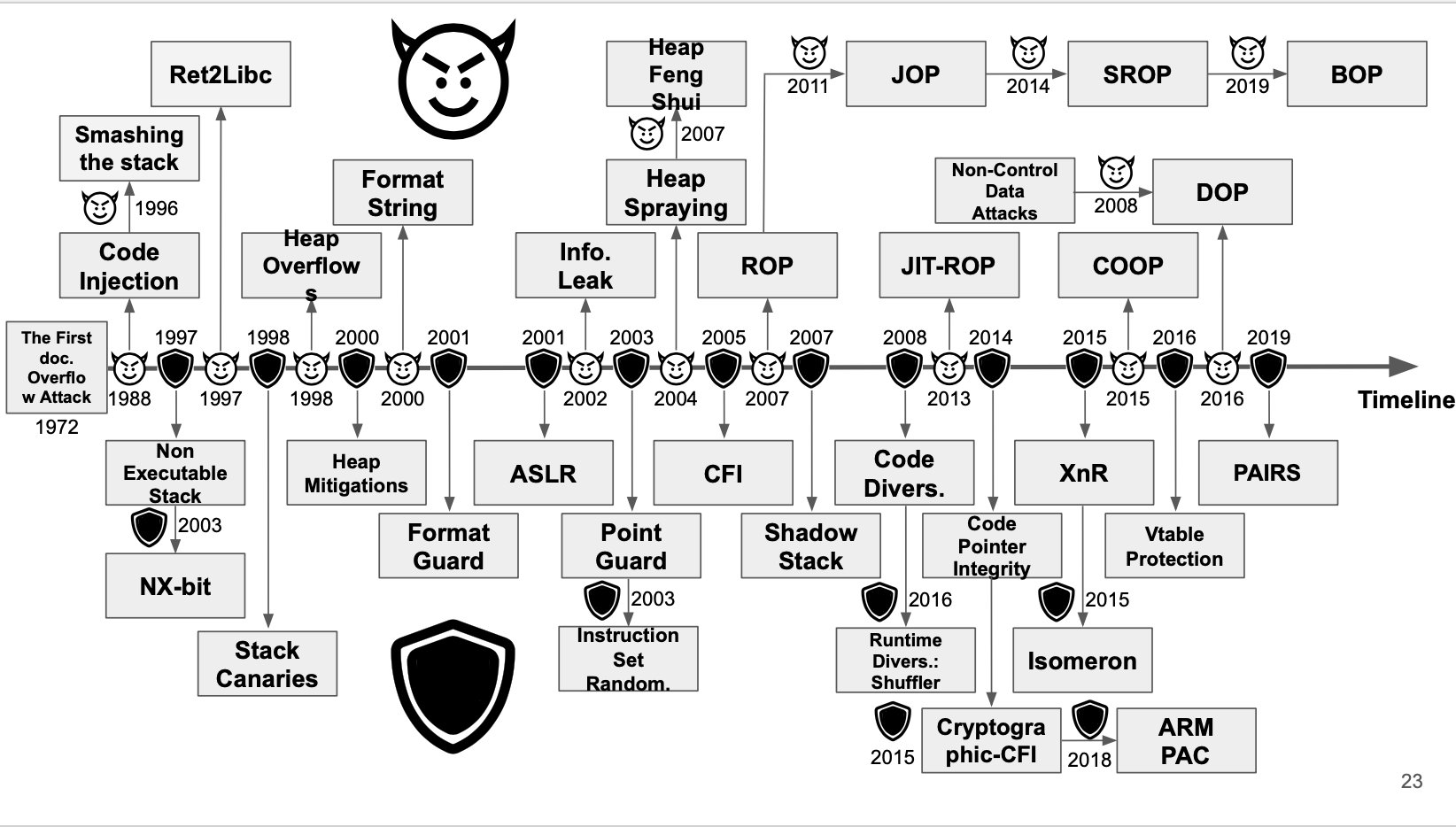
![Fall 23] Lec02: x86_64 / Shellcode / Tools - YouTube Fall 23] Lec02: x86_64 / Shellcode / Tools - YouTube](https://i.ytimg.com/vi/TfHFJa4OMwI/maxresdefault.jpg)