Hack Like a Pro: How to Conduct Active Reconnaissance and DOS Attacks with Nmap « Null Byte :: WonderHowTo

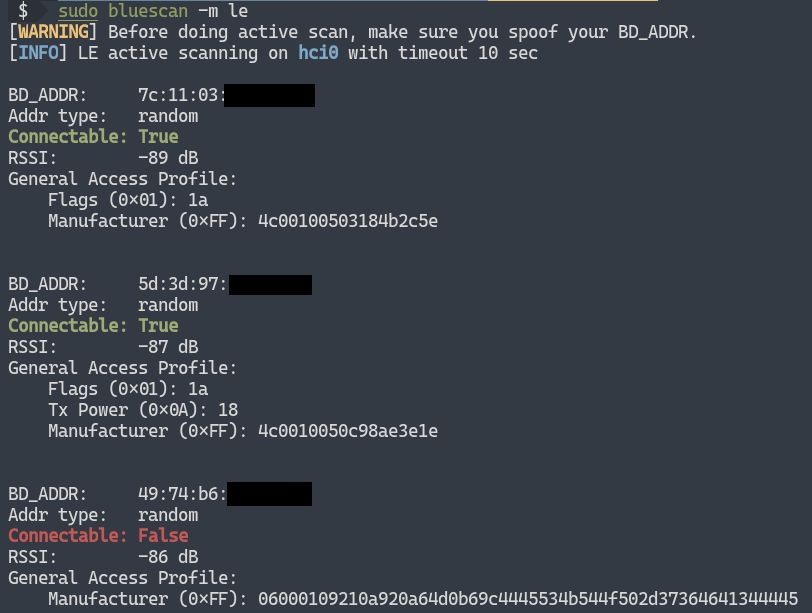
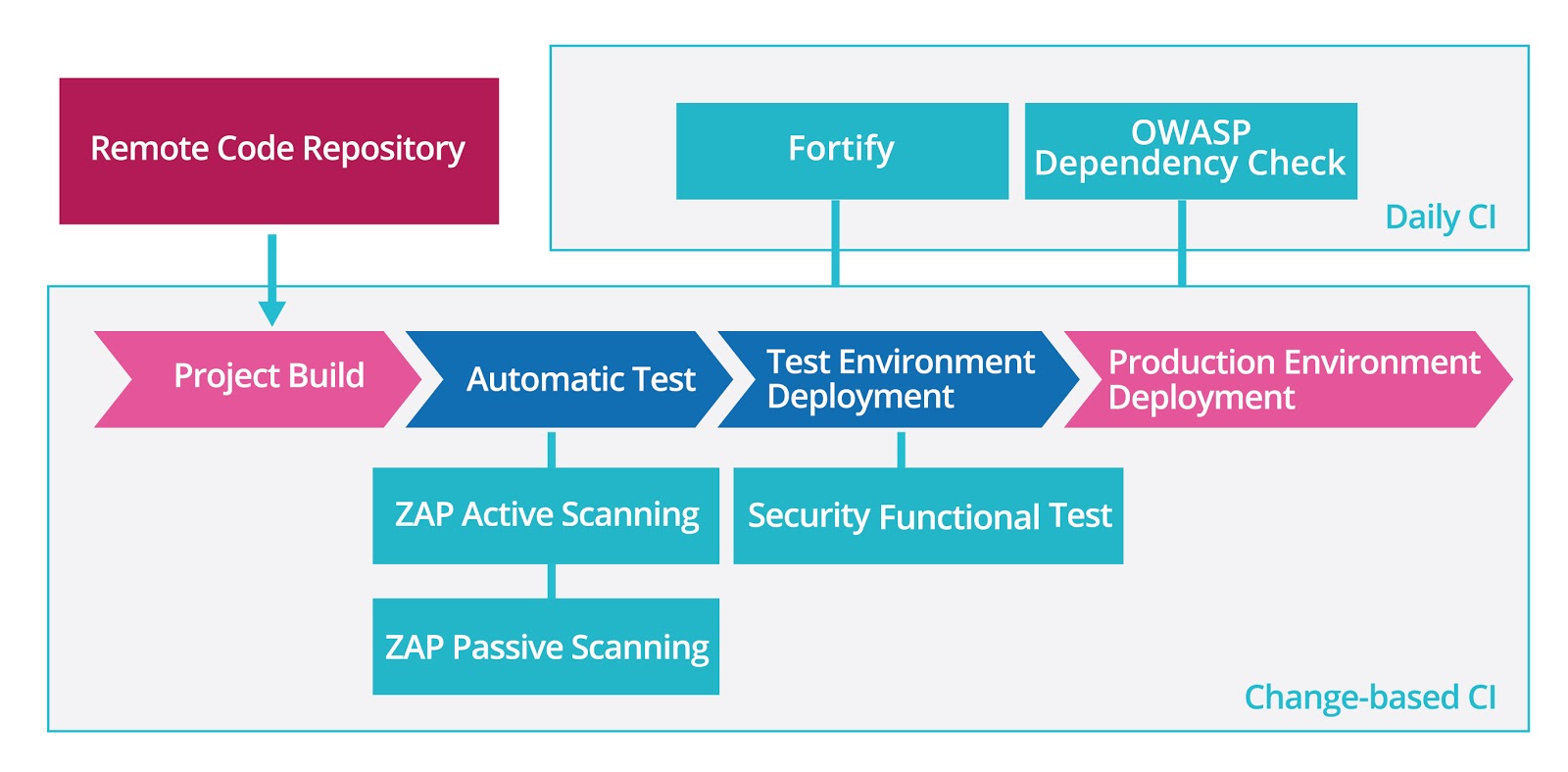
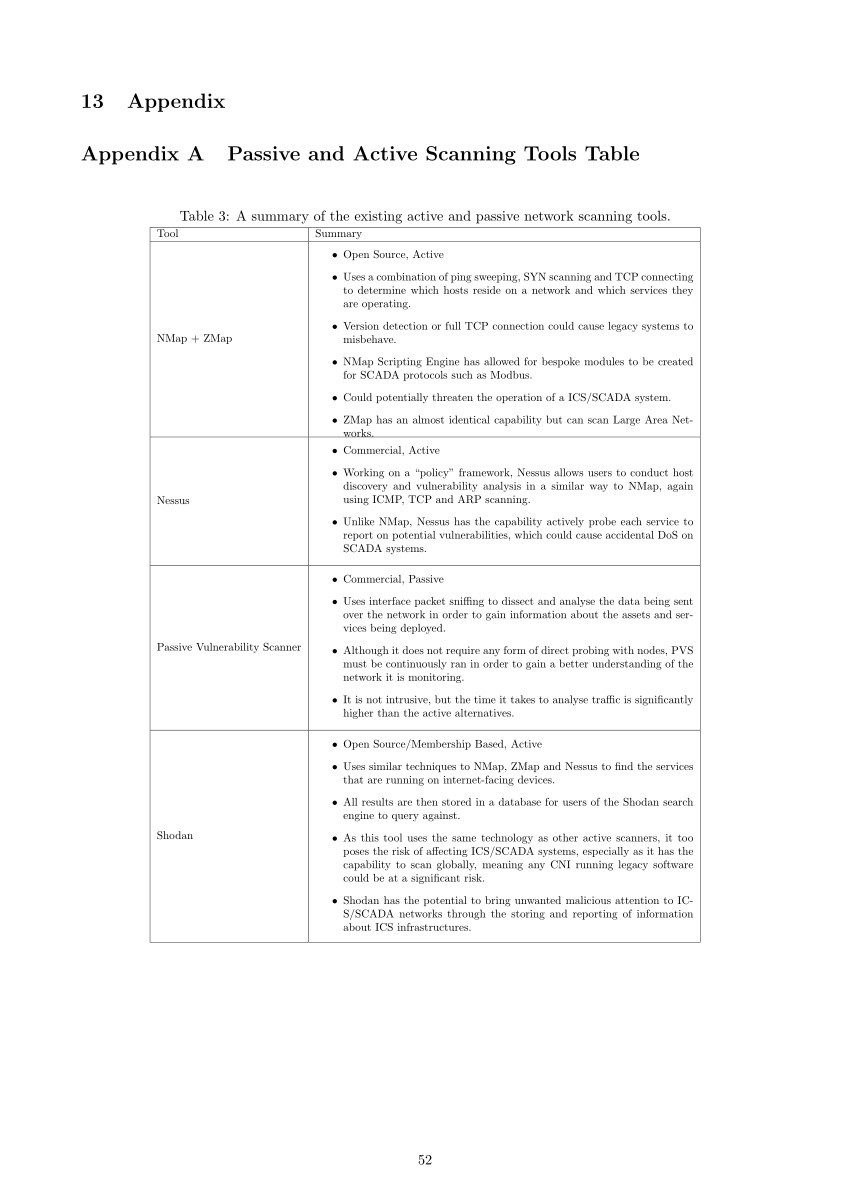
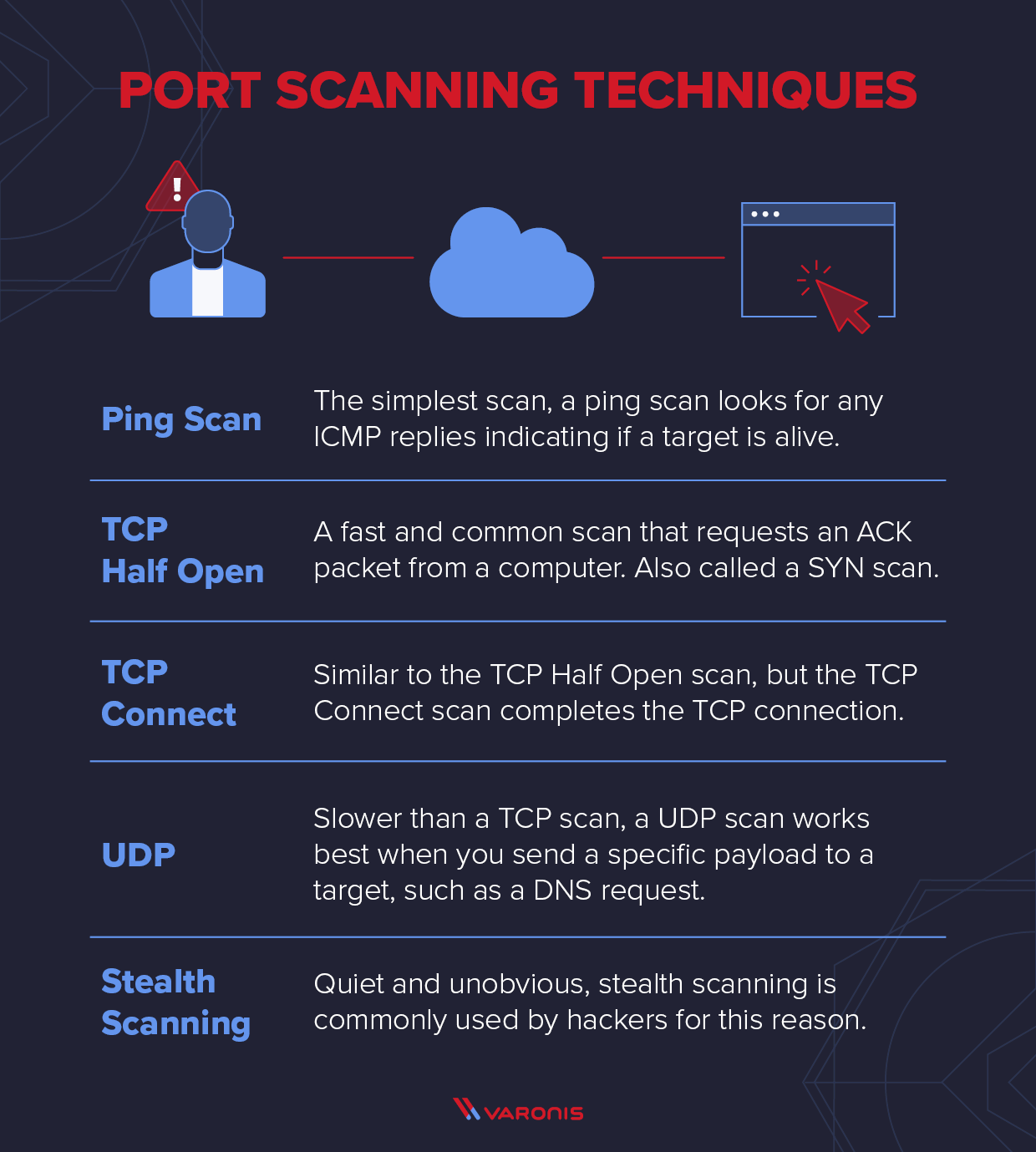
SOLVED: Texts: a) Find any 2 scanning tools other than NMAP and perform various scans at least 5 times. b) Perform 1 Enumeration: NFS Enumeration/SNMP/Active Directory or/Ftp/Telnet enumeration or any other enumeration.